

















 ಎಲ್ಲಾದರು ಇರು ಎಂತಾದರು ಇರು ||೨||
ಎಲ್ಲಾದರು ಇರು ಎಂತಾದರು ಇರು ||೨||ಎಂದೆಂದಿಗೂ ನೀ ಕನ್ನಡವಾಗಿರು
ಕನ್ನಡವೇ ಸತ್ಯ, ಕನ್ನಡವೇ ನಿತ್ಯ
ಕನ್ನಡ ಗೋವಿನ ಓ ಮುದ್ದಿನ ಕರು ||೨||
ಕನ್ನಡತನ ಒಂದಿದ್ದರೆ, ಅಮ್ಮಗೆ ಕಲ್ಪತರು
ಕನ್ನಡವೇ ಸತ್ಯ, ಕನ್ನಡವೇ ನಿತ್ಯ
ಎಲ್ಲಾದರು ಇರು ಎಂತಾದರು ಇರು
ಎಂದೆಂದಿಗೂ ನೀ ಕನ್ನಡವಾಗಿರು
ನೀ ಮೆಟ್ಟುವ ನೆಲ, ಅದೆ ಕರ್ನಾಟಕ
ನೀನೇರುವ ಮಲೆ ಸಹ್ಯಾದ್ರಿ
ನೀ ಮೆಟ್ಟುವ ನೆಲ, ಅದೆ ಕರ್ನಾಟಕ
ನೀನೇರುವ ಮಲೆ ಸಹ್ಯಾದ್ರಿ
ನೀ ಮುಟ್ಟುವ ಮರ ಶ್ರೀಗಂಧದ ಮರ ||೨||
ನೀ ಕುಡಿಯುವ ನೀರ್ ಕಾವೇರಿ
ಪಂಪನ ಓದುವ ನಿನ್ನಾ ನಾಲೆಗೆ
ಕನ್ನಡವೇ ಸತ್ಯ
ಕುಮಾರವ್ಯಾಸನ ಆಲಿಪ ಕಿವಿಯದು
ಕನ್ನಡವೇ ನಿತ್ಯ
ಎಲ್ಲಾದರು ಇರು ಎಂತಾದರು ಇರು
ಎಂದೆಂದಿಗೂ ನೀ ಕನ್ನಡವಾಗಿರು
ಹರಿಹರ ರಾಘವರಿಗೆ ಎರಗುವ ಮನ
ಹಾಳಾಗಿಹ ಹಂಪೆಗೆ ಕೊರಗುವ ಮನ
ಹರಿಹರ ರಾಘವರಿಗೆ ಎರಗುವ ಮನ
ಹಾಳಾಗಿಹ ಹಂಪೆಗೆ ಕೊರಗುವ ಮನ
ಬೆಳ್ಗೊಳ ಬೇಲೂರ್ಗಳ ನೆನೆಯುವ ಮನ
ಮಲೆನಾಡಿಗೆ ಹೊಂಪುಳಿ ಹೋಗುವ ಮನ
ಕಾಜಾಣಕೆ ಗಿಳಿ, ಕೋಗಿಲೆ ಇಂಪಿಗೆ
ಮಲ್ಲಿಗೆ ಸಂಪಿಗೆ ಕೇದಗೆ ಸೊಂಪಿಗೆ
ಕಾಜಾಣಕೆ ಗಿಳಿ, ಕೋಗಿಲೆ ಇಂಪಿಗೆ
ಮಲ್ಲಿಗೆ ಸಂಪಿಗೆ ಕೇದಗೆ ಸೊಂಪಿಗೆ
ಮಾವಿನ ಹೊಂಗೆಯ ತಳಿರಿನ ತಂಪಿಗೆ
ರೋಮಾಂಚನಗೊಳ್ಳುವ ಮನ
ಕನ್ನಡವೇ ಸತ್ಯ, ಕನ್ನಡವೇ ನಿತ್ಯ
ಎಲ್ಲಾದರು ಇರು ಎಂತಾದರು ಇರು
ಎಂದೆಂದಿಗು ನೀ ಕನ್ನಡವಾಗಿರು
ಎಲ್ಲಿದ್ದರೆ ಏನ್ ಎಂತಿದ್ದರೆ ಏನ್
ಎಲ್ಲಿದ್ದರೆ ಏನ್ ಎಂತಿದ್ದರೆ ಏನ್
ಎಂದೆಂದಿಗು ತಾನ್ ಕನ್ನಡವೇ ಸತ್ಯ ಕನ್ನಡವೇ ನಿತ್ಯ
ಅನ್ಯವೆನಲದೆ ಮಿಥ್ಯ

 Always on Time !!..The Transmission control protocol (TCP) Provides applications with reliable ,connection-oriented service and provides full logical path between two hosts on disparate networks .
Always on Time !!..The Transmission control protocol (TCP) Provides applications with reliable ,connection-oriented service and provides full logical path between two hosts on disparate networks .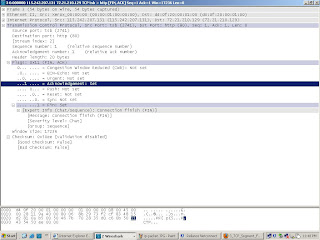



IPsec provides mechanism, not policy: rather than define such-and-such encryption algorithm or a certain authentication function, it provides a framework that allows an implementation to provide nearly anything that both ends agree upon…I mean anything!! J
Terms used in IPSec
AH versus ESP
Authentication Header (AH) "Encapsulating Security Payload" (ESP) are the two main wire-level protocols used by IPsec. Where Authentication Header (AH) only authenticates ..ESP does both the encryption and authentication. Though, they independently used one from another ..Though,we can combine it and use it.
Tunnel mode versus Transport mode
Transport mode only encapsulates IP packets payload (data) ..where, the tunnel mode encapsulates entire IP packet and creates a secure end tunnel between two peers across the untrusted public Network (Internet).
MD5/SHA1 and DES/3DES/AES…
Setting up an IPsec connection involves all kinds of crypto choices ;
Authentication :
Authentication is performs Integrity Check Value (ICV) on the packets needs to be sent based on cryptographic hash algorithm such as MD5 or SHA. It incorporates a secret key only known for both the ends. ..and once packet will reach the destination ICV will be calculated and if the ICV of the sender is same as the recipient that means it successfully authenticated .
AH always provides authentication, and ESP does so optionally.
Encryption:
Encryption is to Modify the packet data in something unreadable format based on algorithms like DES,3DES or AES and which reversible to original format by decrypting these algorithms .
Main mode versus aggressive mode:
"Main mode" requires six packets back and forth, but affords complete security during the establishment of an IPsec connection, while Aggressive mode uses only 3 exchanges providing a bit less security because some information is transmitted in clear text. We will talk it in detail about this …
Main mode is preferred because:
· Main mode is partially encrypted, from the point at which the shared DH key is known to both peers.
· Main mode is less susceptible to Denial of Service (DoS) attacks. In main mode, the DH computation is performed after authentication. In aggressive mode, the DH computation is performed parallel to authentication. A peer that is not yet authenticated can force processor intensive Diffie-Hellman computations on the other peer.
In symmetric cryptographic systems, both communicating parties use the same key for encryption and decryption. The material used to build these keys must be exchanged in a secure fashion. Information can be securely exchanged only if the key belongs exclusively to the communicating parties.
IKE
The goal of the Internet Key Exchange (IKE) is for both sides to independently produce the same symmetrical key. This key then encrypts and decrypts the regular IP packets used in the bulk transfer of data between VPN peers. IKE builds the VPN tunnel by authenticating both sides and reaching an agreement on methods of encryption and integrity. The outcome of an IKE negotiation is a Security Association (SA) .
Need to be noted that this agreement upon keys and methods of encryption must also be performed securely. For this reason IKE is composed of two phases. The first phase lays the foundations for the second.
Diffie-Hellman (DH) is that part of the IKE protocol used for exchanging the material from which the symmetrical keys are built. The Diffie-Hellman algorithm builds an encryption key known as a "shared secret" from the private key of one party and the public key of the other.
IKE Phase I
1.The peers authenticate, either by certificates or via a pre-shared secret.
2.A Diffie-Hellman key is Generated. The nature of the Diffie-Hellman protocol means that both sides can independently create the shared secret, a key which is known only to the peers.
It happens something like this ;
a)From a pool of random bits , each side produces DH private key .
b)Each peer derives a public key from its private key .
c)Public keys are exchanged between these two sites .
d)Each side creates a shared secret from their own private key and the public key received from the peer ( we call it as shared key or DH key.
This DH key is used to exchange
3. Key material (random bits and other mathematical data) as well as an agreement on methods for IKE phase II are exchanged between the peers. It lays the foundation for the IKE Phase 2 (Quick mode/IPSec mode)
IKE Phase 2 :
IKE phase II is encrypted according to the keys and methods agreed upon in IKE phase I. The key material exchanged during IKE phase II is used for building the IPSec keys.
The outcome of phase II is the IPSec Security Association. The IPSec SA is an agreement on keys and methods for IPSec, thus IPSec takes place according to the keys and methods agreed upon in IKE phase II.
How things work in IKE Phase 2 :
a)Peer exchange more key material and agree upon encryption (AES.DES.3DES) and Integrity (MD5,SHA1) methods for IPsec.
b) DH keys created in Phase 1 will be combined with the key materials to produce Symmetrical IPSec key .
c)Symmetric IPsec keys used in Bulk data transfer.
In summary :
1.IKE negotiations builds the tunnel .
2.Ipsec keys used to create encrypted IP Packets for transferring the data.
3.Data payload is encrypted using the various encryption mechanism like DES,AES..
4.Data integrity is ensured with one-way hash functions like MD5,SHA1.
5.Data transfer over the tunnel.
Perfect Forward Secrecy (PFS)
Perfect Forward Secrecy (PFS) refers to the condition in which the compromise of a current session key or long-term private key does not cause the compromise of earlier or subsequent keys. Security gateways meet this requirement with a PFS mode. When PFS is enabled, a fresh DH key is generated during IKE phase II, and renewed for each key exchange.
However, because a new DH key is generated during each IKE phase I, no dependency exists between these keys and those produced in subsequent IKE Phase I negotiations. Enable PFS in IKE phase II only in situations where extreme security is required.

Well. Almost everyone reading this article knows about Computer Viruses. Though its nothing new to us, This article is an attempt to give bit detailed information on this and the Life-Cycle of a Computer Worm ..Life cycle of a computer Virus or Malware is no different from that of a Biological Virus.
Here We go!!
A malware is a program that performs unexpected or unauthorized, but always malicious, actions. It is a general term used to refer to viruses, Trojans, and worms. Malware, depending on their type, may or may not include replicating and non-replicating malicious code.
Due to the many facets of malicious code or a malicious program, referring to it as malware helps to avoid confusion. For example, a virus that also has Trojan-like capabilities may be called malware.
Hence, now we will see what exactly are the difference between a Virus, Trojan and a Malware.
What is a virus?
A computer virus is a program – a piece of executable code – that has the unique ability to replicate. Like biological viruses, computer viruses can spread quickly and are often difficult to eradicate. They can attach themselves to just about any type of executable file and are spread as files that are copied and sent from individual to individual.
In addition to replication, some computer viruses share another commonality: a damage routine that delivers the virus payload. While payloads may only display messages or images, they can also destroy files, reformat your hard drive, or cause other damage. If the virus does not contain a damage routine, it can cause trouble by consuming storage space and memory, and degrading the overall performance of your computer.
A Trojan is a Back-door entry malware that performs a malicious action, but has no replication abilities. Coined from Greek mythology's Trojan horse ( Do you remember that Hollywood flick Troy ?? J ), a Trojan may arrive as a seemingly harmless file or application, but actually has some hidden malicious intent within its code.
Trojan malware usually have a payload. When a Trojan is executed, you may experience unwanted system problems in operation, and sometimes loss of valuable data. Good example is key loggers and Once your computer is compromised with the keyloggers every key stroke on your computer will be logged and the detailed information of whatever you typed (like password) will be stored in the local drive for future access of the intruder or it will be logged and sent to the intruder on the remote location via e-mail .
A computer worm is a self-contained program (or set of programs) that is able to spread functional copies of itself or its segments to other computer systems. The propagation usually takes place via network connections or email attachments.
More recent worms have also discovered ways to propagate using Instant Messengers, via file sharing applications, and by collaborating with other malware such as Trojans or other worm variants. WORM_BAGLE.BE, for example, forms a vicious worm-Trojan cycle with TROJ_BAGLE.BE, in which the worm mass-mails copies of the Trojan, and the Trojan downloads copies of the worm.
Some worms may have an additional payload, such as preventing a user from accessing antivirus Web sites, or stealing the licenses of installed games and applications.
Now let us talk about the Evolution and the Life-cycle of a virus. It includes 5 Phases .
Phase 1 : Creation : To create a Computer Virus/Malware on needs to have the knowledge of coding .Now days , Any one with the basic knowledge of Coding and access to the internet( where you will get plenty of self- tutorial websites teaches how to write a virus )can create a virus.
Phase 2 : Replication and Propagation
Not all the malwares have this Replication and Propagation capabilities .Trojans can be only downloaded from the link or by installing masked application pretending to be the genuine .
While Virus can replicate via E-mails ,IMs or with network shares and some of these has the ability to automated self-replication within a system or network.
Phase 3: Execution
Most malware perform their malicious activities upon execution like opening a unknown .exe file . Some have certain payloads that are activated only at a certain trigger date, or with the onset of a specific trigger condition
Phase 4: Discovery
This phase does not always follow activation, but typically does. When a malware is detected and isolated across the world , it is sent to the ICSA in Washington, D.C., to be documented and distributed to antivirus software developers. Vendors like Symantec or MacAfee or developer’s will create signatures or DAT files based on the pattern of the malware and will be released to the public use with their respective AV products .
At this point, antivirus software developers modify their software so that it can detect the new malware. This can take anywhere from one day to six months, depending on the developer and the malware type.
With the latest up –to-date AV programs on end user machine is the best way to eradicate majority of the Major Malware or Viruses .
Preventive measures;
Proactive or preventive measures are as follow but not only limited to these ;
Make sure you have a very powerful Anti-Virus Software (McAfee Symantec or Trend Micro) running on your system and is up to date with the latest virus definition files .
Make Sure not to visit untrusted websites or download untrusted files from the internet .
Make sure not to open any e-mail attachment from any unknown source.
1.